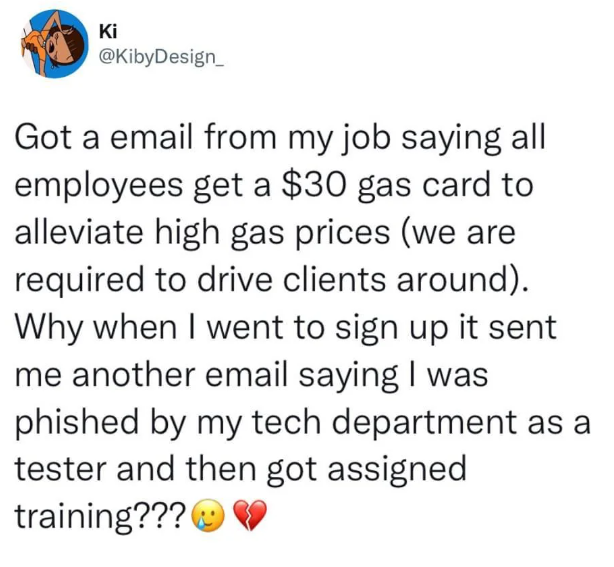
“Here’s an offer for something we know you want and that a respectful employer would provide. Oh, you actually thought your employer respected you? You must be an idiot who needs special training.”
The thing is, there were some hints in the email it wasn't legit, like bad sender or weird links. That was the test. That the employer is bad too, doesn't change the fact the employee fell for the bait.
I feel that if your job requires you to drive, the company would provide the means of transportation. Heck, I work from home and I get to choose between either a company car with a card to fill it up whenever or a pretty roomy budget with a train card.
Having a client in my car would be weird, especially when it smelled like last night’s takeout
This goes especially true for me. "Don't mind the baby seats, you can squeeze in right between them."
That's why you take all the baby clients
It really depends on the company, job, and where you live. I worked as a contractor for a delivery company for a while, putting about 20,000 miles a year on my own car transporting stuff. In the US, if you drive your own car for work, you get a tax deduction for the mileage you put on your car while working. The pay was pretty good and the hours were short, but I was effectively converting the value of my car into cash during that time.
Which is why it's a probable attack vector. You think a malicious actor wouldn't do this?
The only phishing e-mails I receive are from my employer. As a matter of process I report these e-mails like a diligent lackey, then upon receiving an e-mail congratulating me on passing their test, I report that one too. I think the non-test phishing reports undergo manual review so I hope I'm wasting someone's time somewhere in payback.
Still haven't forgiven them for a tone-deaf 'we care about you during COVID' phishing e-mail they sent when everyone was genuinely struggling.
I report any and all emails from anyone on the CSIRT team as suspicious.
They did a phising test targeting every employee without informing me (internal ITSM lead) first. So they deserve the extra work, and my entire team does the same.
Same here, and I got annoyed at these emails filtering through the different rules that I have set up. I realized that the test emails all had some values in the headers to indicate them as such, so I set up a rule to filter them out to a separate folder. It obviously defeats the point, but it's much less annoying.
I just ignore all emails. I have found too many phishing emails and have decided that our systems appear to be compromised. It hasn't improved since I reported them, so I am playing it safe. PM me when you need to communicate, and keep meetings on the calendar, I'll show.
You might have a lot of phishing emails that the company filters out without you ever seeing them. For these tests, they do things to make sure this email will get through, even if the automated filters would have otherwise blocked it.
Companies will do that and then send links with url shorteners for totally legit things and wonder why everyone ignores then.
My company has to send out emails like: "The mandatory training email is not phishing, even though it is flagged [EXTERNAL] by the system."
Me: "That's what a fishing email would say."
We must be coworkers. They literally did this to our group yesterday for an external survey. And I refuse to fill it out.
No, no, the point of the URL shortener IS so that everyone ignores them; they've been trained to. "No one RSVP'd to the pizza party so we canceled it. Also we are a great employer who lists things like Pizza Parties as job perks! They're totally real!"
Sounds about right.
Pro tip, set up a rule in your email client to send any email that contains the following phrases, phishme.com or knowb4, in the header to junk.
Note that I said header, not From field.
It is so stupid that orgs spend thousands of dollars on these products and you can be seen as not being a phishing risk because of their shitty systems.
At my work, we got a phishing email a few weeks before Christmas.
It was for a gift card for a Honey Baked ham.
I was pretty sure it was a phishing test but apparently a lot of people fell for it. Enough so, that a fairly senior colleague blasted an email saying it was in poor taste since it was Christmas and a lot of people could really use it.
I thought that made it more effective training because a scammer would use that, but I also understand that it has the potential to fuck with people's emotions.
Anyway, that started a trend within the company's Teams and social platform, making jokes and sharing memes.
The CEO even emailed, agreeing with the original email blast and then had a real giveaway of honey baked gift cards.
Sounds like a decent CEO.
I got a message saying I needed to sign up and completed a course I'd never heard of so I marked it as spam and deleted it.
Turned out it was genuine...
Last week I came in to work with an email that I received a $100 gift card. I immediately reported it as phishing and went about my day. A few hours later my manager asked if I received an email about said gift card and I told him I reported it. Turns out it was legit and was for good performance. Whoops
I just don't open emails from my company unless the subject has the words Urgent or Action Required and even those I forward to the IT anti phishing email to annoy them, even when I know it's legit.
Now all you get is emails which say urgent, so you don't know which are actually urgent.
So far I've always installed a filter (at work, school, and privately) that removes the "high priority" flag from any mail.
If it can't wait, call me.
In the last two months I have gotten about a dozen emails on my work account that tripped enough red flags for me to think they were phishing attempts. It turns out that they were all legit and failure to respond could be determental to still working there. Good thing our boss was looking out for us.
What I have learned is that I should respond to any half-assed email and ignore the years of annual training I've recieved to the contrary.
I just mark any slughtly fishy mail as phising and send it to the helpdesk. Either I get s thank you back, or a „its legit“. either way, I dont need to worry about it anymore
I've definitely gotten good at identifying phishing attempts from our Cybersecurity team.
I'm on our cybersecurity team and our last phishing sim was so real looking and legit sounding I thought it was real, and I knew the phish was coming. The only indicator was the sender email was a slight misspelling of Microsoft. I pointed out that that phish is not a fair phish, our users are not going to meticulously examine every email for microscopic indicators. Half if them are barely tech literate, but they're doctors or nurses and only know what they need to know to do their job. Our cybersecurity lead was completely in "wtf are you talking about? From Micrasoft.com is totally illegitimate" mode, I had to point out that our users flag 70% of the emails as phish, and phishing tests that look like completely legitimate emails aside from a single character out of place in an obscure location most of our users aren't even thinking if looking at undermine legitimate emails and increase our workload b/c we've trained our users to think every email is a phish test from cybersecuriry.
I don’t see the problem, is that not the point of phishing tests? Users need to ensure the sender is legitimate before taking action such as clicking links.
good way to get me to ignore all emails
Sounds like phishing tests are just the company outsourcing spam filtering to their own employees instead of paying for a spam filtering service of their own.
They do this at my work. I simply report every external email I get as a phishing attempt.
As a result, I've caught all the fake phishing emails sent by our IT department, at the minor cost of them having to clear 50+ legit emails per day. My coworkers have been quite appreciative of my tactics against phishing, and have started to adopt my methods.
Strangely enough, the number of phishing tests IT has sent out has dramatically decreased since I was initially hired.
My company sent one of these out made to look like a survey on employee thoughts and opinions on their compensation - a very real issue in our company that I suspect they just wanted to try and condition people not to talk about.
Replied back to let them know as such and to inform them it was an asshole move and I would not be completing their training. Was worth the HR write-up - fuck those suits, too.
Corporate does this all the time to at my work.
The GM of my office came talk to me because I had actually won like employee of the quarter or something, but when I got the email with the "redeem here for your $50 gift card" I reported it as phishing. I asked him why they couldn't just go to the grocery store and hand me a physical gift card, he blinked for a moment like that hadn't occurred to him. I showed him the quarantined emails I get on Outlook every day from dozens of phishing attempts made to my work email everyday.
Companies are damned if they do and damned if they don't. All the best security on the world will never prevent an attack from the universally weakest link - humans.
Best you can do is identify the humans that are likely to fall for it and remind them to be extra careful when clicking links in emails.
We also have anti fishing campaigns in our company and usually I do pretty well with those, but last year because of a running event they sent a mail out in regards to free T-shirts for the event. Most of the company including me failed gloriously.
You guys read your emails?
Lol that person is stupid. these test phishing mails are super easy to spot. I hope they don't work in tech
You can tell it's fake because it suggests that corporate would just hand you a new benefit out of the blue.
This likely had several warning signs that can be used for even personal emails. 1) is it too good to be true? Definitely in this example. Give me a gas card physically and I might believe it. 2) look at the actual link before you click. If it's not part of the main domain for the company you're expecting, or not within the intranet at work, it's an automatic nope. 3) any oddities in the message or images that seem wrong. Misspellings, pixelated logos, etc. This is the smallest red flag, as often times getting a perfect email without any grammar or spelling issues means it didn't come from a manager, that seems to be a requirement.
phish tests are redundant after a point. I flagged the first few but they upped the frequency so much it got ridiculous. Turns out the header for the phishing tests all contains the name of the testing company. New phish tests are re directed to my brownie points folder, so I just have to worry about the real thing now
All emails get automatically forwarded to the IT department, for "suspected phishing". If it is from a known internal source, especially so.
[Moved to !iiiiiiitttttttttttt@programming.dev, check pinned post.] iiiiiiitttttttttttt.
you know the computer thing is it plugged in?
Moved to !iiiiiiitttttttttttt@programming.dev.