Wow, it's pretty wild they didn't even attempt to encrypt or protect this data, even if it is local to your machine. What a treasure trove for malware to sift through.
It IS encrypted. Not well, but it's encrypted.
I thought that it was encrypted if your home directory was encrypted? The impression that I got was that it was just a SQLite database stored in the clear. The user must certainly be able to make queries of that database in order for it to work, so even if it's hosted by a non-user service, malware running locally will still be able to exfiltrate the data.
All true, which is what I meant by "not well" encrypted. It's technically encrypted, but for all practical purposes it might as well not be.
Now ransomware hackers can sell all your shit to someone else if you refuse to pay.
Please go through the FAQ section of the git project. It's an eye-opener.
Q. Does this enable mass data breaches of website?
A. Yes. The next time you see a major data breach where customer data is clearly visible in the breach, you’re going to presume company who processes the data are at fault, right? But if people have used a Windows device with Recall to access the service/app/whatever, hackers can see everything and assemble data dumps without the company who runs the service even being aware. The data is already consistently structured in the Recall database for attackers. So prepare for AI powered super breaches. Currently credential marketplaces exist where you can buy stolen passwords — soon, you will be able to buy stolen customer data from insurance companies etc as the entire code to do this has been preinstalled and enabled on Windows by Microsoft.
I doubt that. It’s preinstalled and enabled for personal users.
Even if it is enabled by default on pro/enterprise, there will probably be a group policy to disable it.
It feels like this was intended for buisnesses to monitor for phrases on your screen like "coolmath games unblocked free"
or to extract and upload a summary of what happened every second of every day to the server defined in the group policy.

For the kids
Sony BMG copy protection rootkit scandal
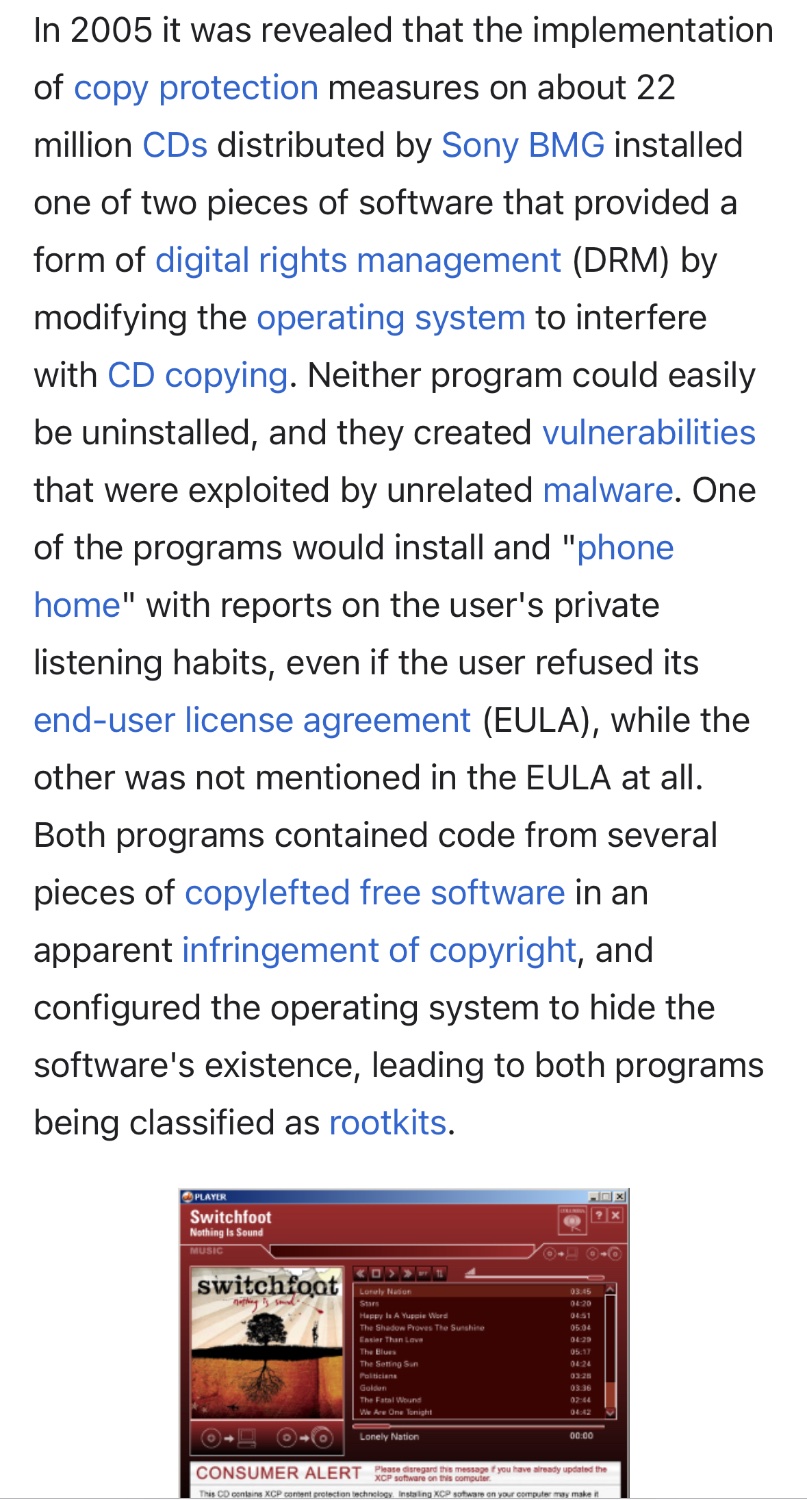
Morons:
Sony BMG initially denied that the rootkits were harmful. It then released an uninstaller for one of the programs that merely made the program's files invisible while also installing additional software that could not be easily removed, collected an email address from the user and introduced further security vulnerabilities.
That’s wild. I’m surprised I never heard of this. Straight up malware.
In a just society the Sony execs would have been jailed for CFAA violations.
Very specific, but makes sense


Hilarious to me that it OCRs the text. The text is generated by the computer. It's almost like when Lt. Cmdr. Data wants to get information from the computer database, so he tells the computer to display it and just keeps increasing the speed
there are way more efficient means of getting information from A to B than displaying it, imaging it, and running it though image processing!
I totally get that this is what makes sense, and it's independent of the method/library used for generating text, but still...the computer "knows" what it's displaying (except for images of text), and yet it has to screenshot and read it back.
It happens the same on android for some reason
Like 5-8 years ago the google assistant app was able to select and copy text from any app when invoked, I think it was called “now on tap”. Then because they’re google and they’re contractually obligated to remove features after some time, they removed this from the google app and integrated it in the pixel app switcher (and who cares if 99% of android users aren’t using a pixel, they say). The new implementation sucks, as it does ocr instead of just accessing the raw text…
It only works fine with us English and not with other languages. But maybe it’s ok as it seems that google’s development style is us-centric
Now on Tap also used OCR. Both Google Lens and Now on Tap get the same bullshit results on any languages that are not Latin. Literally, Ж gets read as >|< by both exactly the same.
They changed it, in the beginning it was using the text and not ocr
For example this app could be set as assistant and get the raw text https://play.google.com/store/apps/details?id=com.weberdo.apps.copy
But only the app set on system as assistant can do it
I was very disappointed when they changed it around 2018 as it produced garbage in my language when it was working so good…
Having worked on a product that actually did this, it's not as easy as it seems. There are many ways of drawing text on the screen.
GDI is the most common, which is part of the windows API. But some applications do their own rendering (including browsers).
Another difficulty, even if you could tap into every draw call, you would also need a way to determine what is visible on the screen and what is covered by something else.
Hey, yeah… why aren’t they just tapping the font rendering DLL?
…are they tapping the front rendering dll??
That's the thing, it doesn't really know what it's displaying. I can send a bunch of textboxes, but if they're hidden, or drawn off-screen, or underneath another element, then they're not actually displayed.
Text from OCR is one kind of match. Recall also runs visual comparisons with the image tokens stored.
Imagine how easy is the life of law enforcement now.
Before if they seized a laptop encrypted with bit locker they could not do anything.
Now they just need to ask Microsoft the encryption password, which is automatically and silently saved in the Microsoft account (now mandatory) and they can have all the history of what the subject of the investigation did in the past years
What? Bitlocker key tied to MS account and mandatory? What's the point of encryption if the key isn't secret any more?
To protect against casual theft of a device causing the data to be in the thief's hands in addition to the actual device.
The average person unfortunately is not likely to properly backup their encryption keys so if they forget their password (or don't use one and rely on the default of just TPM), they'll complain about losing their data. Having the key backed up gives them a way to get their data back in non-theft situations.
I like how people on lemmy seem to only think of the high stakes state sponsored theft. And not the theft that’s thousands of times more common.
Yeah. Most theft targets the hardware, not the data within.
It’s secret to most, not all.
In a hilarious and infuriating side note, MS is obviously doing their absolute best to blame-shift here.
It’s code. It’s a project someone made to graphically illustrate and demonstrate, in the wild, why the entire concept of MS Recall is an absolutely awful, foundationally-flawed idea. It is not a “hacker tool”. The MS c-suite and board members are just pissed that stock go down as a result of their stupidity, and they’re looking for people to blame who aren’t themselves.
MS is obviously doing their absolute best to blame-shift here
There is not a single word in that article that says anything about blame shifting. That title was written by wired.com
So . . . MS wants to force Recall on us.. Assures us that it's "secure." And it can't be bothered to even lightly encrypt the data? This is just plain incompetent.
Also, MS want to bundle CoPilot with Office 365, a subscription service. You will be paying for the privilege of spying on yourself.
What an unexpected turn of events.

Imagine if they zero day this.
Lol "if". This thing is going to be a massive target.
Someone has already demonstrated using an off-the-shelf infostealer to steal the Recall database from a test computer. It won't take any special skills or technology for this to be a problem.
I was gonna make a joke on how there's no root on windows, but then I remembered sudo for windows is now a thing so.......
sudon't please --pretty
Windows be like

good luck to people typing their passwords in visible mode
Windows, pretending it can't read what you're typing in because you didn't click "show password":
That was quick.
Iirc chrome stores your local cookies/session in a place malware could also attack. Probably the same idea for other browsers.
I'm not sure I fully understand the issue here. If we're ok with that info being trivially retrievable by a bad actor, why isn't this ok?
Like I get you may not like it, and it's a target, but there are already lots of targets that have gotten a pass based on user permissions. Is it just the breadth of potential info? With the cookies you could potentially log into someone's bank account.
First, false equivalency.
Second, we’re not okay with cookies and session being in a place that could leak — it’s why we’re doing everything possible to stop that from happening (I mean GDPR alone is one effect of this).
Third, the fact that you can’t see a difference between cookies, which actually can be secured via proper encryption and signing, and a literally unencrypted database driven by OCRed screenshots (taken every couple of minutes) that requires an opt-out and is a very small slippery slope to that data making its way back to Microsoft’s own servers for their own greedy pursuits….then I’m not sure what to tell you.
Recall is wrong. And it’s indefensible. Period.
If you think it’s okay, then feel free to open everything up to Microsoft of who you are and what you do on your Copilot+ PC. I, for one, among many, will choose to secure my information as best as possible, including never using another Microsoft product again, if at all possible. And I’ve already done so for myself.
browser data is a potential liability, sure, but you have tools to manage it. you can delete pages or entire websites, you can use private windows, you can purge history older than 6 months or something like that, and at least a few browsers have a "forget" button that wipes out the last two hours of history. similar deals with cookies and other data, and we've collectively decided the benefit of having browser data is worth the risk.
not so here. Recall is a record of everything you've ever done on your PC. you can't selectively delete things like you can with browser history, the app and website exclusion is only as good as whatever Recall is using to detect apps and websites, and you can't redact sensitive info after the fact. people are generally okay with browser history and data because they know they have fine-grained controls to manage it, controls Recall doesn't have
Technology
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related news or articles.
- Be excellent to each other!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, this includes using AI responses and summaries. To ask if your bot can be added please contact a mod.
- Check for duplicates before posting, duplicates may be removed
- Accounts 7 days and younger will have their posts automatically removed.