368
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
this post was submitted on 01 Dec 2025
368 points (100.0% liked)
Mildly Interesting
23633 readers
43 users here now
This is for strictly mildly interesting material. If it's too interesting, it doesn't belong. If it's not interesting, it doesn't belong.
This is obviously an objective criteria, so the mods are always right. Or maybe mildly right? Ahh.. what do we know?
Just post some stuff and don't spam.
founded 2 years ago
MODERATORS
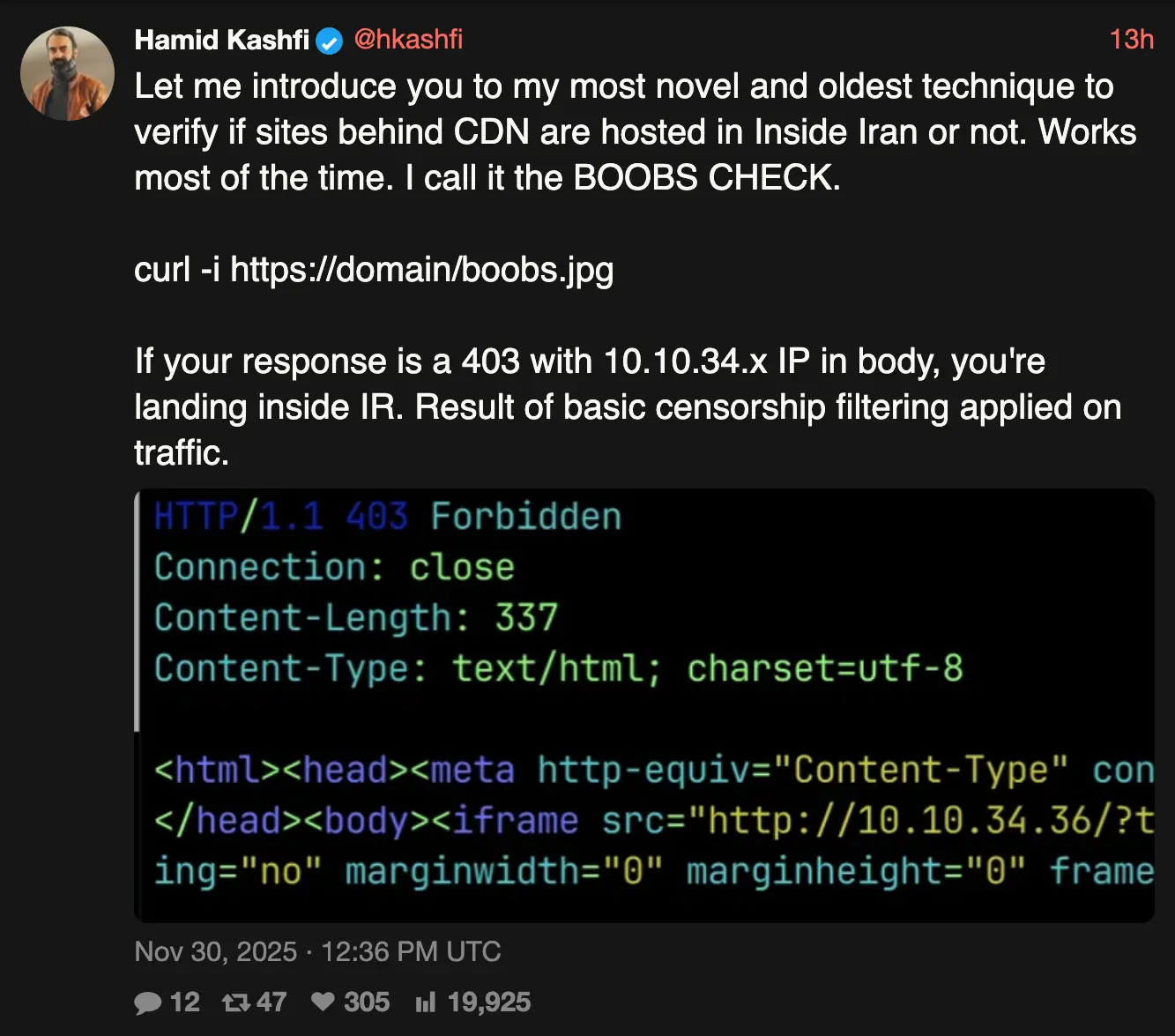
My original guess was that they're intercepting DNS, but since boobs is in the path, it wouldn't be sent. How does this work?
Don't know if this is entirely accurate, but Wikipedia has article about it.
They are giving response codes like 403 so it's not a failure to resolve and I agree it's not DNS... It's behaving differently based on different sub pages so it's something underneath the https encryption. Maybe an intermediary WAF that decrypts? Maybe some weird server side tooling that has govt provided?
I would guess WAF but I'd love to hear from someone who actually knows.
It’s either
Right? If it were an unencrypted HTTP GET request, then every router on the way would see the plaintext string
boobsin the URL and therefore intercept it.If I had to guess, Iran has so few landline connections that they man-in-the-middle every TLS connection they can by either forcing every server to hand over their private key files (difficult) or by forcing a certificate authority trusted by default Web browsers (there's a lot of them) to issue certificates for every top level domain they see in SNI data attached to encrypted packet headers; the latter method need not even require participation by Iranian servers, so long as the traffic is bottlenecked for man-in-the-middle attacks and outsiders don't question unusual certificate authorities being used.